SSL VPNs (Secure Socket Layer Virtual Private Networks)
Security is key when accessing remote devices. The basics, such as changing default passwords, locking down ports and switching off unnecessary services, are all good practices for locally securing a device. A system must nevertheless deal with outside efforts that may disrupt data transmission, or in the worst case, destroy it.
A few methods of transportation are available for remote communication. It can be over public or private infrastructure, with encryption playing a crucial role in both. One way to isolate access to external threats is to set up a private infrastructure using either cellular or fixed-line technology. Essentially, the network will operate like the Internet, but will only be available to a specific customer. This can allow interconnectivity between a top-end system and remote devices, with the addition of privacy. Despite this, the information transmitted between these locations is not encrypted or secure.
The Internet is also a very suitable method of communication over public infrastructure. One of the biggest challenges is that transmission between the top end and remote sites will not be private. With the right tools, anyone can monitor and observe traffic. This is why you should always use encryption and a virtual private network (VPN).
There is no preference for using either the public or private networks. Public Networks, such as the Internet, have billions of secure communications between sites in existence. Private networks can be seen as expensive for the privilege of privacy but no encryption.
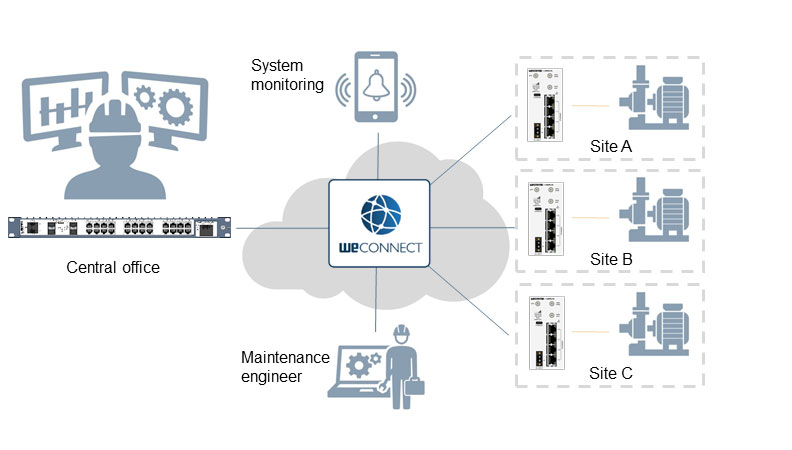
The use of VPNs and protocols such as Secure Socket Layer (SSL) makes communication more secure. Certificates are used in SSL to ensure trust between Site A & Site B. The trust is based on public and private keys, where the public key is shared, but the private key is not. The public and private keys are verified regularly on each device, to ensure their validity within the infrastructure. WeConnect is an example of SSL encryption which is used on many mission-critical networks in industries such as Oil & Gas, Shipping, Power, Water & Wastewater and Aviation.
Managing the certificates requires a trusted authority. One of the biggest advantages of SSL is the ability to distribute and revoke certificates. The certificates will be updated periodically to ensure the network is secure and communication is uninterrupted. When an authority notices suspicious activity, they can revoke the certificate, making it invalid and issuing a new one. Using this method, data can be transported securely over a public network, such as the Internet. As a result, Site A and Site B remain operational.
Regardless of the method you choose to use, the Merlin range has it covered. When using public or private infrastructures, SSL VPNs with cellular connectivity provide remote outstations with added protection.

Featured product
The robust and compact Merlin 4400 cellular router is the ideal fit for utility and industrial applications. Featuring zero-touch large-scale deployment and comprehensive cybersecurity capabilities, such as secure boot and TPM (Trusted Platform Module).
Learn more
Cloud based networks
System administrators and engineers can access the system from the comfort of their homes to manage, monitor and support remote sites.

On premise router connectivity
Remote locations, even if they are sometimes in undesirable areas, can now be brought on to the network for greater visibility.

SSL VPNs
The use of VPNs and protocols such as Secure Socket Layer (SSL) makes remote communication more secure.

Remote diagnostics and support
System administrators and engineers can access the system from the comfort of their homes to carry out diagnostics and support.
Explore all remote access solutions
For decades we have offered products and solutions for remote access networking applications. Our extensive product range and deep understanding of applications ensure that we can offer the best solution for your needs.

Remote access for utility applications
Cellular connectivity enables the ability to monitor sites holistically.

Remote access for industrial applications
Gain an overview of sites that were either once manned or relatively invisible.

Cyber-securing remote networks
Keeping your remote industrial networks and systems secure has never been more critical.

Zero touch networks
Cost effectively deploy and carry out maintenance of thousands of routers.

Protocol conversion
Protocol conversion enables one common stream of data to be transmitted or received to the top-end SCADA.

Legacy modem replacement
Migrate legacy serial devices from dial-up or leased line modem communications to serial over IP broadband.
Nuri Shakeer
International sales

For support inquiries, click here to contact Technical Support
